Risk and Security
Real-time visibility into your environment, allowing you to quickly identify and respond to potential threats
Streamline identity workflows, enhance security, and
achieve compliance with a SaaS-deployed solution
Overview
Omada Identity Cloud is a full-featured IGA-as-a-service solution built to meet all your business needs. With highly customizable workflows, automation options, and no additional code required, our cloud-based solution improves operational efficiencies, strengthens your security posture, and provides full visibility into your environment. Omada Identity Cloud is the only IGA solution that can be rapidly deployed in 12 weeks, ensuring the fastest time-to-value.
Omada Identity Cloud meets the security, compliance, and efficiency needs of business leaders by providing a comprehensive and automated approach to identity and access management. Our modern IGA solution can help save time and money, while also improving the security and compliance of your organization.
Real-time visibility into your environment, allowing you to quickly identify and respond to potential threats
Stay compliant with comprehensive and automated user access overview, ensuring that users only have access to the resources they need to do their jobs
Accelerate the business through improved provisioning, seamless workflows, optimized helpdesk capacity
Features
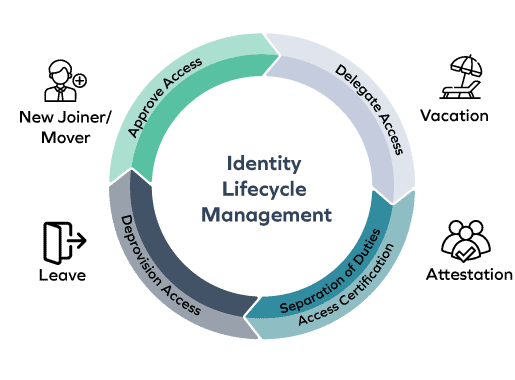
Omada Identity Cloud provides a comprehensive solution for identity lifecycle management, covering joiner, mover, and leaver processes for all identity types. We provide a more efficient and secure identity management process by automating policy and role management and offering unified provisioning across IT systems.
Omada Identity Cloud’s workflow engine provides you with highly adaptable process flows tailored to your unique business needs, supporting manual, triggered, or scheduled workflows. We provide pre-configured email integration and prompts, facilitating seamless communication and ensuring efficient task management within your organization.
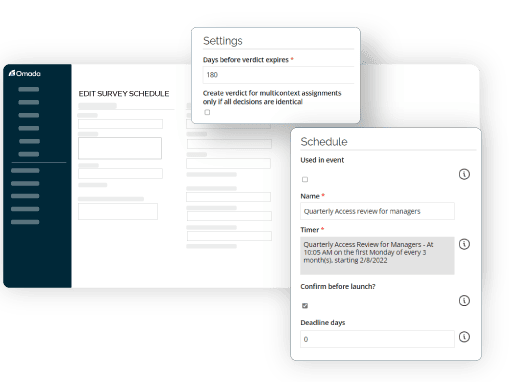
Omada Identity Cloud provides configurable certification surveys for user entitlement, account, and permission reviews. These certifications can be event-triggered or scheduled for periodic re-certification. We also offer central monitoring for streamlined oversight, bolstering security and compliance.
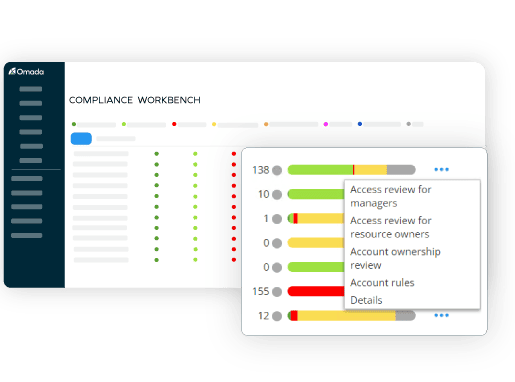
Omada Identity Cloud provides strong compliance and risk mitigation with comprehensive reporting and audit trails, user-friendly dashboards, and baked-in risk scoring that supports proactive risk management within approval workflows and access reviews. With the Omada Compliance Workbench, you have full visibility into the compliance level of each onboarded application and system. The Workbench also empowers you to take immediate remedial actions, ensuring that any issues are promptly addressed.
Our Differentiators
Analytics that improves decision-making, decreasing manual efforts to improve the TCO of your program
Automation of processes and workflows that can be configured without the need for code development
Compliance dashboard with drill-down actions and Control Policies that detect risks and enable remediation
Deliver operational IGA and a clear roadmap for maturity to get maximum ROI from your investment
Create, configure, upgrade, restore, and clone environments via an industry-leading management portal or via API
Omada Identity Cloud has the highest availability for the SaaS Identity Governance market
Standards-based framework leveraging SCIM, OData, REST, SOAP and SQL enables fast connectivity
The IdentityPROCESS+ framework provided out of the box to aid the delivery of a successful IGA deployment


OMADA IDENTITY CLOUD
Experience identity governance at the speed of business. Our AI-powered platform ingests data in real-time, surfacing risks and streamlining workflows, all while offering flexible connectivity across your identity fabric. Make informed decisions, empower users, and achieve operational efficiency – all with Omada Identity Cloud, your intelligent identity advantage.
Use Cases
Omada Identity Cloud is the all-in-one solution that perfectly aligns with your business needs, offering comprehensive support for identity lifecycle management.
Onboarding and managing employee access is simple with Omada Identity Cloud. With automated provisioning and de-provisioning, role-based access control, and self-service capabilities, you can efficiently grant and revoke permissions, ensuring your workforce has the right access to the right systems at the right time.
Omada proactively mitigates security risks by enforcing strong access controls, continuous monitoring, and real-time threat detection. With advanced analytics and user behavior profiling, you can identify and respond to potential threats before they become a problem, safeguarding your organization’s sensitive data and assets.
Effortlessly meet regulatory requirements and industry standards with the Omada Compliance Workbench. Our solution offers separation of duty (SoD) policy enforcement, comprehensive audit trails, and reporting capabilities, giving you the confidence that your identity governance practices align seamlessly with the ever-evolving compliance landscape.
“Omada covers your full identity management lifecycle easily. The system really delivers on Omada’s promises.”
“The solution covers all our use cases without having to write and maintain any code.“
"Omada is very user-friendly and at the same time a powerful tool that has so far answered 99% of our IAM needs!"
“Great IGA Software solution for the enterprise. Helps keeping your organization secure.”
Integrations
With an extensive library of out-of-the-box connectors, Omada Identity Cloud seamlessly integrates with your other solutions. Maximize the value of your current investments while leveraging our robust identity and access management capabilities to enhance efficiency, security, and compliance across your entire ecosystem.
With a wide variety of fully configurable connectors, Omada makes it easy to securely onboard systems. See how simple it is to add a new system to Omada.
Omada Identity Cloud is based on over 20 years of experience and delivery of rapid and reliable identity results that give organizations the maximum value for their identity governance investment.
FEATURED RESOURCES
Dive into Omada Identity Cloud with our interactive product tours. These self-paced demos offer a glimpse into Omada's intuitive interface and powerful features that streamline the entire identity lifecycle.
Omada provides the most comprehensive IGA as-a-Service solution on the market. In this product brief, you get an introduction to Omada Identity Cloud.
Legacy IGA systems pose challenges and scalability restrictions to growing businesses. A modern cloud-based IGA solution can improve your organization's security, compliance, and efficiency.
Let us show you how Omada can enable your business.