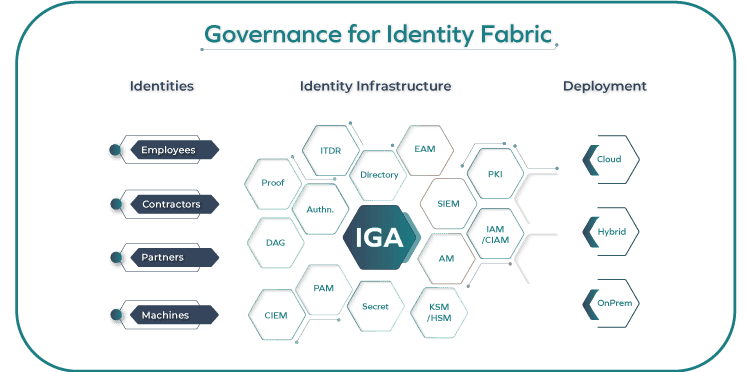
Reshape your IAM strategy with a focus on identity fabric governance. Discover how an identity governance-first mindset and use case-driven evolution can revolutionize your approach to governance.
- Products
Modern IGA Solution That Can Be Deployed in 12 Weeks
• Full-featured IGA
• Configurability without code
• Best-practice framework for solution design and deploymentSecure Digital Identities for All Users, Applications, and Data• High degree of configurability
• Intelligent compliance
• Manage identities and access across hybrid platforms - Services
Best-Practice Processes and Standardized Implementation
• Support at every step of your IGA journey
• Personalized service package to accelerate your deployment
• Avoid common pitfalls and get value in 12 weeksProven Project Implementation Methodology• Iterative implementation roadmap
• Standardized, well-documented best practices
• Support from Omada-certified project managers, architects, and consultantsContinuous Support for Ongoing Success• Stellar Customer Success Team
• Quick and professional Service Desk
• Access to ITSM system and KPI reportsIdentity Governance Training for Progressive Skill Building• Digital self-paced and instructor-led courses
• Training on demand through our Premier Academy subscription
• Individual, role-based learning plans and certification pathsOmada Identity Cloud Accelerator Package• Ensure fast and successful IGA deployment
• 5-step process with clear exit criteria
• 12 weeks time to value - Solutions
Identity Governance: The Strategic Tool That
• Helps support enterprise IT security
• Makes it easier to meet compliance mandates
• Automates access provisioning and enables the workforce from day 1360° Overview of Identities and Access• Automated access provisioning and deprovisioning
• Least privilege and separation of duties policies
• Simple-to-run certification campaignsFull Compliance Overview and Audit Trail• Access compliance status dashboards
• Cross-system certification campaigns
• 50+ audit report templatesAutomated IGA Best Practices• Identity lifecycle management
• Automatic access provisioning
• Self-service access requestsIdentity Fabric and the Role of IGAOmada provides Governance for Identity Fabric ensuring compliance regulations are met, security and efficiency around identity workflows are maintained.
- Resources
IdentityPROCESS+

A definite guide to Identity Governance and
Administration best practices. Learn how to
successfully deploy and maintain an IGA solution.Gartner Market Guide for Identity
Governance and AdministrationIn this Guide, Gartner has identified Omada as a
Representative Vendor in IGA. Use it to evaluate top
Identity Governance vendors and anticipate future
trends, features, and capabilities in the IGA market.How to Overcome Challenges Moving
Legacy IGA to the CloudFamiliarize yourself with the typical threats that
can derail a seamless legacy to cloud migration of
IGA functionality and get tips on managing them.DEKRA
As part of their digital transformation, DEKRA moved
from an in-house access management solution to
a modern, cloud based Omada IGA solution.5 Reasons to Prioritize IGA Today
Get practical examples and data proving the
value of IGA and learn the five key reasons you
must make it a business imperative today.Product Briefs
We are constantly adding new features to Omada
products to ensure your IGA efforts keep pace with
the ever-evolving threat landscape.Product News
Get information about the newest Omada product
features, benefits, and use cases to ensure you get
the most from your IGA program.Interactive Product Tours
Participate in interactive product demos covering
capabilities such as Delegate Access, Request
Access, Approve Access Request, and more.Webinars
Get the latest IGA trends, information, and intelligence
from renowned industry experts in Omada’s live and
on-demand webinar presentations. - Company
We are Omada

A market-leading provider of identity governance
and administration solutions. Get to know us better!Become a key part of something special
At Omada, efficient teamwork creates extraordinary results.
We enable talented people to create career paths where
they can thrive, be inspired, and have fun.World-class support and technical
expertise - right in your communityOmada partners provide unmatched advisory, product
and service re-sale, and project delivery resulting in
unsurpassed customer satisfaction scores.Leading organizations doing more with identity
Don’t just take our word about the value of Omada
solutions. See what actual users think.Omada is making news!
See what the media are reporting about our
innovative identity governance solutions.Come see us!
We frequently deliver expert presentations, exhibit, and
run demos at the world’s leading security and IGA events.
Look at our upcoming schedule to see if we cross paths –
we'd love to speak with you.Omada Wins "Overall ID Management
Solution of the Year" AwardOmada is a winner for a third consecutive year in the 7th
annual CyberSecurity Breakthrough Awards program.We can help
Omada is a global market leader in Identity Governance.
Please reach out to us with questions or to get more information.
- Products
Modern IGA Solution That Can Be Deployed in 12 Weeks
• Full-featured IGA
• Configurability without code
• Best-practice framework for solution design and deploymentSecure Digital Identities for All Users, Applications, and Data• High degree of configurability
• Intelligent compliance
• Manage identities and access across hybrid platforms - Services
Best-Practice Processes and Standardized Implementation
• Support at every step of your IGA journey
• Personalized service package to accelerate your deployment
• Avoid common pitfalls and get value in 12 weeksProven Project Implementation Methodology• Iterative implementation roadmap
• Standardized, well-documented best practices
• Support from Omada-certified project managers, architects, and consultantsContinuous Support for Ongoing Success• Stellar Customer Success Team
• Quick and professional Service Desk
• Access to ITSM system and KPI reportsIdentity Governance Training for Progressive Skill Building• Digital self-paced and instructor-led courses
• Training on demand through our Premier Academy subscription
• Individual, role-based learning plans and certification pathsOmada Identity Cloud Accelerator Package• Ensure fast and successful IGA deployment
• 5-step process with clear exit criteria
• 12 weeks time to value - Solutions
Identity Governance: The Strategic Tool That
• Helps support enterprise IT security
• Makes it easier to meet compliance mandates
• Automates access provisioning and enables the workforce from day 1360° Overview of Identities and Access• Automated access provisioning and deprovisioning
• Least privilege and separation of duties policies
• Simple-to-run certification campaignsFull Compliance Overview and Audit Trail• Access compliance status dashboards
• Cross-system certification campaigns
• 50+ audit report templatesAutomated IGA Best Practices• Identity lifecycle management
• Automatic access provisioning
• Self-service access requestsIdentity Fabric and the Role of IGAOmada provides Governance for Identity Fabric ensuring compliance regulations are met, security and efficiency around identity workflows are maintained.
- Resources
IdentityPROCESS+

A definite guide to Identity Governance and
Administration best practices. Learn how to
successfully deploy and maintain an IGA solution.Gartner Market Guide for Identity
Governance and AdministrationIn this Guide, Gartner has identified Omada as a
Representative Vendor in IGA. Use it to evaluate top
Identity Governance vendors and anticipate future
trends, features, and capabilities in the IGA market.How to Overcome Challenges Moving
Legacy IGA to the CloudFamiliarize yourself with the typical threats that
can derail a seamless legacy to cloud migration of
IGA functionality and get tips on managing them.DEKRA
As part of their digital transformation, DEKRA moved
from an in-house access management solution to
a modern, cloud based Omada IGA solution.5 Reasons to Prioritize IGA Today
Get practical examples and data proving the
value of IGA and learn the five key reasons you
must make it a business imperative today.Product Briefs
We are constantly adding new features to Omada
products to ensure your IGA efforts keep pace with
the ever-evolving threat landscape.Product News
Get information about the newest Omada product
features, benefits, and use cases to ensure you get
the most from your IGA program.Interactive Product Tours
Participate in interactive product demos covering
capabilities such as Delegate Access, Request
Access, Approve Access Request, and more.Webinars
Get the latest IGA trends, information, and intelligence
from renowned industry experts in Omada’s live and
on-demand webinar presentations. - Company
We are Omada

A market-leading provider of identity governance
and administration solutions. Get to know us better!Become a key part of something special
At Omada, efficient teamwork creates extraordinary results.
We enable talented people to create career paths where
they can thrive, be inspired, and have fun.World-class support and technical
expertise - right in your communityOmada partners provide unmatched advisory, product
and service re-sale, and project delivery resulting in
unsurpassed customer satisfaction scores.Leading organizations doing more with identity
Don’t just take our word about the value of Omada
solutions. See what actual users think.Omada is making news!
See what the media are reporting about our
innovative identity governance solutions.Come see us!
We frequently deliver expert presentations, exhibit, and
run demos at the world’s leading security and IGA events.
Look at our upcoming schedule to see if we cross paths –
we'd love to speak with you.Omada Wins "Overall ID Management
Solution of the Year" AwardOmada is a winner for a third consecutive year in the 7th
annual CyberSecurity Breakthrough Awards program.We can help
Omada is a global market leader in Identity Governance.
Please reach out to us with questions or to get more information.