Let's Get
Started
Let us show you how Omada can enable your business.
Accelerate your IAM projects with a proven process framework
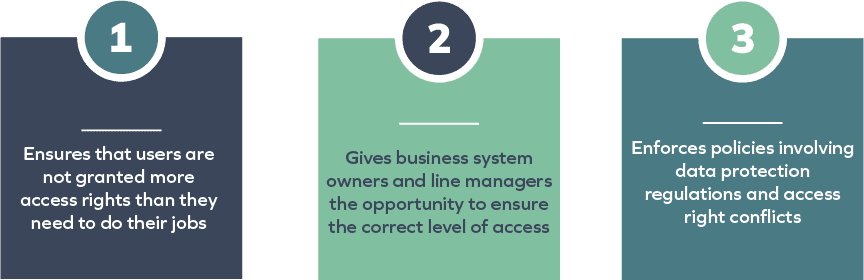
Throughout an organization it can be extremely complex to document who has access to what and why they were granted that access. Governance ensures that identities are not granted more access than they need to do their jobs, gives application, system owners and line managers the opportunity to ensure the correct level of access, and enforces policies involving data protection regulations and access right conflicts.
Business processes for governance allow organizations to verify who has access to what information, remove access that is no longer needed, produce real-time and historical audit reports and ensure that Separation of Duty (SoD) policies are properly enforced.
Administrators and security practitioners need to evaluate access rights on a regular basis, otherwise users will accumulate access to more systems than they need as they change roles. Governance processes also allow for un-owned accounts (orphaned accounts) to be reassigned or deleted. Administrators can also ask data owners and managers to assign different risk classifications to data held within their respective systems. Finally, verifying that the actual state of access and entitlements matches the desired state is key to maintaining good governance.
Access rights that are granted to users, either when they join a company or when they request new access rights, may not be required for the entire employment lifecycle. If the access rights are not evaluated on a regular basis, users typically accumulate access to more systems than they need. The governance processes let administrators verify with the business system owners or employee line managers that the access users have is appropriate for their current jobs.
If an account is found to have no owner assigned to it (a so-called ‘orphan account’) because an employee has left the company, then governance processes allow for the ownership to be reassigned or for the account to be deleted as appropriate.
In addition to managing access to systems, access to different types of data needs to be controlled. The governance processes allow administrators to ask data owners and managers to assign different risk classifications to data held within their systems. Once these classifications are assigned, data access can be governed in accordance with various global data protection regulations and other relevant data protection standards.
Verifying that the actual state of access granted to users matches the desired state that defines a compliant and secure system is a key process to maintaining good governance. If inconsistencies are found, they are flagged to the administrator, so they can be resolved either by approving or revoking the access.
In addition, the governance processes include workflows to manage the separation of duty (SoD) rules so toxic combinations of access rights are not assigned to an individual, thus preventing the ability to carry out fraudulent activities.
The Governance process area includes the following process groups and subprocesses:
As part of Omada IdentityPROCESS+, an identity governance framework focusing on best practice processes, there are several key components to Governance that are critical to follow best practices to ensure business efficiency is optimized, security is tight, and compliance is met.
Setting up reports that can provide a sense of what is actually happening is critical for success. Real-time dashboards allow organizations to understand their current access compliance situation so that they can maintain compliance. Reporting within Omada can also process extra data from the data repository to show information about relevant objects and provide a comprehensive data overview. This view allows organizations to see who has or has had, access to what, why, and when that access was granted, who approved it, and when it was revoked.
After reports have been set up, regularly verifying that access rights, policies, role definitions, and master data in Omada are still valid is up next. Certification campaigns (also called reviews, attestations or re-certifications) are used to periodically validate the information in Omada. Omada administrators can define the purposes of the campaign, including what data is to be certified, who should certify it, and how often a survey should run directly in the portal. The administrator can also input what should happen when responses to the survey are submitted, or when answers are not given, as well as set notifications and reminders to be sent, and determine who can monitor and manage the campaigns and surveys.
The survey administrator can initiate and assign surveys to the relevant managers or survey owners. This includes determining when the survey starts, monitoring its ongoing progress, reassigning questions if needed, generating and sending reports and closing the survey. IdentityPROCESS+ lays out how surveys are created in the design certification campaign process and scoped based on factors such as risk classification, systems and resource types for maximum effectiveness.
When the campaign is launched by the administrator the certification task is sent to the manager for review, so as to enable responses. Once they receive the task to recertify data (i.e. access rights for managed identities), the reviewer reviews the data and submits answers to the questions. If unable to answer some of the questions, the survey can be reassigned to another user (if the survey admin has permitted this action when launching the survey).
When someone leaves the company or changes roles, the organization must transfer ownership of certain objects to another human identity. This automatically starts a workflow, which allows resource owners to propose new owners, who can accept or reject the proposal.
As part of the ongoing process to review access, administrators and practitioners should regularly review access rights assigned to all identities. Access reviews are initiated either on a scheduled basis or done ad hoc manually by system owners or administrators. They can then verify accounts by system, organizational unit, specific resources, compliance status, or classification tags. Direct assignments are expired and deprovisioned immediately, and if a kept assignment already has a desired state it will remain as is.
Blog
4 Tips for Certification Campaigns
Access certification campaigns are a way for organizations to audit entitlements and formally validate that identities’ access rights are appropriate. Here are 4 tips for building successful certification campaigns.
Omada can check if the desired security and compliance state matches the actual access granted to system resources. If there is a mismatch, the differences need to be promptly rectified to maintain both security and compliance. Omada compares the defined desired state with actual state gathered from target systems and graphically displays compliance status; whether it is ‘under control’ or not, whether it has been explicitly, or implicitly approved. Other potential states include not approved, orphan assignment, pending deprovisioning, in violation, or implicitly assigned.
Applying classification tags to identities, systems, resources, resource folders, contexts and other objects means they can be identified when specific company processes need to be applied. This also helps to manage resources differently depending on the types of data being stored, the sensitivity of the information, and any regulations governing their use. Data administrators can create classification tag categories in Omada. For example, the classification category ‘GDPR’ could be populated with tags ‘personal data’ ‘personal sensitive data’ ‘high-risk data’ ‘low-risk data’ etc., thereby allowing administrators to manage different types of data according to internal policies and external requirements.
Administrators can identify data that is held in different resources so it can be managed with the appropriate levels of security/compliance policies defined by the organization. When classification tags and tag categories are set up, data objects are tagged using a classification survey. These tags and tag categories are used to establish and operationalize the risk management strategy and put relevant controls in place. This also allows the administrator or system owner to create a survey which is sent to users, presenting them with tasks to classify the survey. Once the questions are completed, the classifications need to be approved by the category owner. Once approved, classification tags are added or removed to/from the object.
Webinar
Certify Access with Regularity (and Confidence!)
Watch this on-demand webinar to learn how to create successful access certification campaigns and effectively run them across multi-cloud environments.
A critical component of Governance is the evaluation of separation of duty policies to ensure that individuals are not granted toxic combinations of access rights that enable them to commit fraud. Administrators can create new constraint policies to determine whether toxic combinations of access rights have been assigned, can detect violations, and allow managers to evaluate the situation. Omada evaluates user identities for violations, and if found, the automated workflow sends the task to the manager for approval. If approved and a compensating control is selected, access is provisioned. This is also automatically logged and stored.
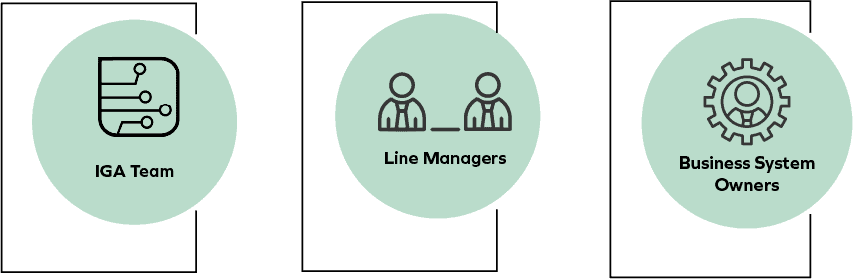
Within IGA processes, it is critical that multiple stakeholders are aligned and working together. For Governance, the following teams must be involved.
Below are a set of key best practice recommendations that should be taken into consideration when implementing the governance processes in IdentityPROCESS+.
It is important to determine which KPIs need to be measured, monitored and reported on. For administration of the IGA system, this will include system KPIs such as spare database storage capacity, response times, and resource usage. To monitor use of the IGA system from a business perspective, KPIs such as identities being managed, the number of assignments, and unresolved accounts need to be considered. When considering the KPIs required, it is important to
involve stakeholders from the business such as line managers, the compliance team, and external auditors as they may have additional requirements.
When considering KPIs and reports, it is highly recommended that organizations start with the out-of-the-box options provided by the IGA solution rather than
reinventing the wheel and creating their own. Most organizations find that the standard reports satisfy most of their needs and therefore only need to create a small number of additional customized reports. The process of determining whether the out-of-the-box reports are suitable for the organization could take up to a year to complete if there are many stakeholders with different requirements.
To ensure good governance, it is important to establish a rigorous set of certification campaigns. The frequency of certification campaigns should be based on the criticality of the application and any external compliance regulations that need to be taken into consideration. For example, access to a critical banking application may need to be recertified every 6 months whereas a less critical application such as the HR holiday booking system may only need access recertification every 12 months. When determining the frequency of recertification, the audit team should be consulted as they may have specific requirements.
To effectively perform user access recertification, organizations should determine how surveys should be run. This includes who owns the surveys, who starts them, and who follows up if they are not answered. When deciding who should manage surveys, political considerations need to be taken into account – for example, a senior executive may not appreciate being sent a reminder from a junior employee for not completing answers to a recertification campaign they have received.
The governance processes enable organizations to maintain compliance over user identities for the entire lifecycle of employment. They allow administrators to continuously monitor for orphan accounts and put measures in place to prevent toxic access combinations causing separation of duty violations.
By implementing the IdentityPROCESS+ governance processes, organizations will maintain a secure and compliant organization while being able to effectively support the granting of access rights to end users.
Throughout an organization, it can be extremely complex to document who has access to what and why they were granted that access. Business processes for governance allow organizations to verify who has access to what information, remove access that is no longer needed, produce real-time and historical audit reports and ensure that SoD policies are properly enforced.
An identity governance framework operates by providing a set of rules, practices, and processes that guide how an organization is directed and controlled. The framework defines the roles and responsibilities of various stakeholders, such as the board of directors, management, and employees, and establishes the systems and processes necessary to ensure effective decision-making, risk management, and compliance.
Key elements of an identity governance framework include:
An identity governance framework helps to ensure that the organization is operating in an ethical and responsible manner and is aligned with its objectives and legal and regulatory requirements.
Identity governance frameworks are becoming increasingly common in organizations around the world. While the adoption of identity governance frameworks varies by industry and region, many organizations are recognizing the importance of having a structured approach to governance in order to operate more effectively and reduce risk.
In some industries, such as financial services and healthcare, identity governance frameworks are mandated by regulatory authorities as a way to ensure that organizations are operating in a safe and sound manner. In other industries, such as technology and manufacturing, identity governance frameworks are being adopted voluntarily as a way to improve performance and reduce risk.
In recent years, there has been a growing recognition of the importance of corporate social responsibility and sustainability, and many organizations are adopting governance frameworks that include these elements as a way to demonstrate their commitment to these issues.
While the adoption of governance frameworks may vary by industry and region, they are becoming increasingly common as organizations recognize the benefits of having a structured approach to governance.
Signs that suggest a governance strategy is working effectively include:
1. Clear roles and responsibilities: A successful governance strategy will clearly define the roles and responsibilities of different stakeholders, such as the board of directors, management, and employees. This helps to ensure accountability and effective decision-making.
2. Robust identity governance: A successful governance strategy will have effective processes in place for identifying, assessing, and managing risks. This includes establishing risk tolerance levels and developing risk management plans as well as procedures to address specific compliance requirements. These processes will be specifically reflected in any governance reporting you do.
3. Alignment with strategic objectives: A successful governance strategy will be aligned with the organization’s strategic objectives. This ensures that governance practices are supporting the organization’s goals and priorities.
4. Effective communication: A successful governance strategy will involve effective communication between stakeholders, including the board of directors, management, employees, and external stakeholders. This helps to ensure that everyone is aware of their roles and responsibilities and that decisions are made in a transparent and accountable manner.
5. Continuous improvement: A successful governance strategy will include processes for continuous improvement. This includes monitoring and evaluating the effectiveness of governance practices and making changes as necessary to ensure that they remain effective and aligned with the organization’s objectives.
Following these governance best practices will drive the success of your strategy.
Implementing a governance program at your business can be a complex process, but the following steps can help to guide you through the process:
1. Conduct a governance assessment: The first step in implementing a governance program is to assess your current governance practices. This includes reviewing your current policies and procedures, identifying any gaps or weaknesses, and determining areas for improvement.
2. Develop a governance framework: Once you have assessed your current governance practices, you can begin to develop a governance framework. It should include the policies, procedures, and processes necessary to ensure effective identity governance.
3. Establish a governance committee: To oversee the governance program, you should establish a governance committee. This committee should include members from the board of directors, management, and other stakeholders. The committee should be responsible for monitoring and overseeing the governance program, ensuring that it is effective and aligned with the organization’s objectives.
4. Develop policies and procedures: With the governance framework in place, you can begin to develop the policies and procedures necessary to implement the governance program. This includes policies and procedures for risk management, compliance, ethical conduct, and performance monitoring.
5. Communicate the governance program: Once the governance program is in place, it is important to communicate it to all stakeholders, including employees, customers, and suppliers. Creating a governance report is an integral part of this process. It will explain the governance framework, policies, and procedures and ensure that everyone understands their roles and responsibilities.
6. Monitor and evaluate the governance program: To ensure that the governance program remains effective, it is important to monitor and evaluate its performance on an ongoing basis. This includes regularly reviewing policies and procedures, monitoring performance metrics, and making changes as necessary to ensure that the governance program remains effective and aligned with the organization’s objectives.
Let us show you how Omada can enable your business.