Identity-related security risks do not emanate from a single source. There are many threat vectors, both within and outside of an organization. In Q4 of 2023, Omada surveyed more than 550 IT security and business leaders and learned which identity-related security threats present the greatest concern. Download The State of Identity Governance 2024 to read the complete findings.
In the Decoding the State of IGA 2024 webinar, Omada Vice President of Product Strategy Rod Simmons and Senior Solution Architect Craig Ramsey broke down the data and suggested how organizations should use the findings to inform their plans for making their identity governance solutions more effective. Simmons and Ramsey then asserted that the threat of identity-related security breaches should be a top-of-mind consideration at all levels of every organization; from individual users right up to C-level executives. Simmons and Ramsey then went on to explain that to address these threats effectively, organizations must have appropriate identity controls in place across their entire IT infrastructure.
In this post, we’ll explain why a modern IGA is particularly effective for mitigating two specific identity-related security threats that surfaced during the webinar.
Modern IGA Users Have More Confidence in Their Ability to Mitigate Specific Cybersecurity Risks
To explain the findings about specific identity-related concerns succinctly enough to make them actionable, Simmons and Ramsey explained how the respondents of the survey are placed into two main cohorts; organizations using legacy or “homegrown” Identity Governance and Administration (IGA) solutions and those having acquired and deployed modern IGA stack. They then expanded that these groups are from organizations that are very concerned with identity-related threats and the data suggested that organizations using a modern IGA solution have more confidence in their technology capabilities to neutralize identity-related security threats across the board than those using legacy or homegrown IGA solutions.
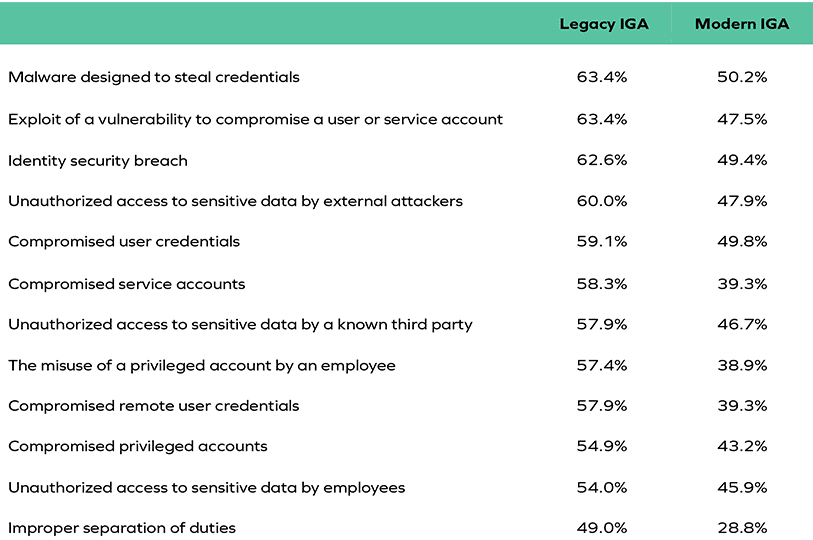
Figure 1: Specific identity-related threats about which organizations are “very concerned”
Modern IGA Is Better at Mitigating Improper Separation of Duties (SoD) Risks
Simmons and Ramsey point out that one of the identity-related threats with the largest “concern delta” is improper separation of duties (SoD). An SoD policy requires administrators to define one or more conditions that specify which combinations of permissions and roles users are not permitted to hold. In most instances a single condition suffices, but organizations are finding that in more scenarios, they must define multiple conditions to cover more complicated combinations.
The data suggests that organizations believe that a modern IGA stack does a much better job of enforcing SoD policies than legacy or homegrown systems. When users have just the ability to access what they need, both the likelihood and impact of a potential breach decrease dramatically. Effective enforcement of SoD policies combined with a solution that enables adherence to the principle of least privilege will result in an organization being able to reduce the attack surface. This approach must include the ability to clean up dormant, orphan, and unused user access rights.
A modern Identity Governance solution creates a control plane that includes access management with other modern IGA capabilities like identity lifecycle management, access request, access review, violation management, role management, auditing, and reporting to overcome the challenge of siloed identity information and provide a genuinely holistic approach to managing identity-related risk.
The Modern IGA Effect on Mitigating the Risk of Compromised Service Accounts
Another identity-related threat with a significant “concern delta” is compromised service accounts. Organizations have wanted to automate credential changes of service accounts for a long time. Historically, this was an error-prone process where administrators would scramble the credential and update a service account, but not update all the different components that were used in that service account across the enterprise. There were dependencies and administrators needed to restart services, and people would not hit their Service Level Agreements as a result. The process has matured tremendously in the recent past and it’s more locked down than ever before. Modern IGA solutions are better at helping organizations determine what kinds of activity security teams should expect from service accounts and what normal behavior is so they can identify abnormal behavior.
Expert, Data-Driven Advice on Managing Your IGA Strategy
In our webinar, Decoding the State of IGA 2024, Omada Vice President of Product Strategy, Rod Simmons and Senior Solution Architect Craig Ramsey break down the findings regarding enterprise perceptions of identity governance from The State of Identity Governance 2024 report. Exclusively on the webinar, they expand on insights uncovered and provide key takeaways to help shape your organization’s identity and access management strategy.
Watch this webinar on-demand to learn more
This is the second of a four-part series covering the highlights of Omada’s webinar, Decoding the State of IGA 2024. Read the first blog in the series, Why 100% of IT and Business Leaders Should Be Concerned About Identity Governance in 2024 here.

























