Identity governance and compliance professionals often tell us they are considering Identity Governance and Administration (IGA) capabilities from a single vendor to cover their IAM vendor that provides all their Identity Access Management technology on a single platform. On the surface, working with a single vendor seems more efficient; and when the IGA piece of the platform is included in the system it looks like a cost-effective way to manage identity governance. However, Omada’s research demonstrates that organizations evaluating modern IGA solutions are far more likely to choose best-of-breed technology over the offerings of a single IAM platform vendor.
In this post, we’ll examine the findings of The State of Identity Governance: 2024 to see how IT professionals and business leaders in 567 enterprises with more than 1,000 employees are approaching the move to a modern IGA. We’ll also present the principal factors that drive the decision to adopt a best-of-breed IGA solution to help improve identity security posture across the enterprise.
What the data tells us about best-of-breed IGA technology vs. a vendor offering an IAM platform
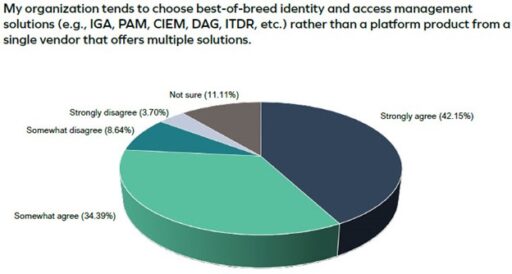
As we can see in the figure below, more than three in four IT professionals and business leaders report their organizations tend to choose best-of-breed solutions over a pure-play IAM vendor. At first glance, a single platform seems like a better decision, but some downsides frequently make this choice more costly eventually. We will take a closer look at these.
Source: The State of Identity Governance: 2024
Why IAM solutions from a single vendor can be more costly
A single-vendor IAM solution seems to build simplicity into identity access management, covering multiple aspects of an identity fabric. As a practical matter, however, the benefits are more than offset by the potential limitations. For example, as your business evolves your IGA requirements may outweigh your single solution provider’s ability to address them. Once your organization commits to a solution, adding outside systems that could improve IGA functionality is more difficult, and migrating to a new solution can be expensive. This tends to happen because the vendor lacks sufficient connectivity to a wider tapestry of identity solutions focusing instead on its capabilities. The result is costly vendor lock-in.
Choosing a cloud-native IGA solution that performs identity lifecycle management, access management, business alignment, and identity security breach response in cloud-hosted, on-premises, and hybrid environments enables you to maintain optimal functionality as your business needs get more complex without relying on a single vendor to make it a priority.
IGA may not be a priority in a single vendor’s IAM platform
Organizations using a single vendor IAM platform are frequently compelled to live with inferior technology that may increase identity-related risks. This is due to how this platform was established. In many cases, these platforms stem from the result of acquisitions that hobble together the appearance of a platform when in reality it’s less of a single platform approach and more of a single pricelist approach.
Just because the vendor claims they will cover your requirements does not make it so in these situations. Verify that it is possible to manage the identity lifecycle, automate provisioning and de-provisioning, enable self-service access requests and approvals, execute role mining and management, implement separation of duty policies and constraints, and simplify the password change process for identities and applications without development. The workaround in many cases can be costly relying heavily on help desk support which is prone to human error, causes lost productivity, and slows down the business process.
Costly compliance with a single vendor IAM platform
As your organization’s technology portfolio expands, identity management complexities grow. A single-vendor platform approach may not be able to keep up with new access management processes and entitlements. Integrating a best-of-breed IGA solution into a cohesive Identity Fabric ensures you have a 360-degree view of all identity-related activities, enabling effective audit processes. Automatic closed-loop compliance enables your organization to “self-heal” gaps in identity entitlements and access, improving cost efficiency. This proactive approach eliminates compliance, audit, and assessment failures by ensuring complete visibility and control over identity-related processes.
The first casualty of innovation is identity security
As your organization evolves, your existing identity security controls may become less effective. This is particularly true with an IAM platform that may be unable to keep up. As you add identities and applications, your environment becomes less transparent to a single vendor platform, and blind spots are created, resulting in critical gaps in your security workflows. Here again, the workaround is manual processes that drain resources and time.
Using a best-of-breed IGA solution ensures you have visibility into risks and compliance by unifying information from the security landscape through bi-directional context exchange. Your solution must be able to extend identity governance to any application, including third-party applications and mobile devices, providing a seamless and frictionless user experience across your entire environment. Unlike a single vendor platform, a best-of-breed IGA solution that is part of a Governance for Identity Fabric approach overcomes limitations with a Connectivity Framework that connects and configures a wide range of applications. This level of visibility supports faster human decision-making and automates repetitive processes wherever possible. This result is increased efficiency in identity workflows, dramatically less manual effort, and far fewer errors.
New complexities demand innovative new approaches to IGA
If your organization is struggling to manage identity governance in today’s dynamic business landscape, see how Omada’s approach to confidently working with Identity Fabric enables organizations to streamline identity processes, mitigate risks, and optimize costs. Omada’s best-of-breed solution leverages tools and advanced technologies, including machine learning and artificial intelligence, to automate workflows and enhance decision-making.
Omada’s Governance for Identity Fabric enables you to:
- Ensure compliance with regulatory requirements and mitigate audit failures
- Improve cost efficiency through automation and closed-loop compliance
- Make informed decisions to effectively mitigate identity risks
Get Omada’s Governance for Identity Fabric solution brief today and see how this proven approach to identity governance can help you.