
Flexible by design
Deploy CAG alongside the systems you need to govern. Run on your preferred OS, hypervisor, or in containers. It is flexible and extensible across environments. Rollout is simple and automatic updates keep operational overhead low.


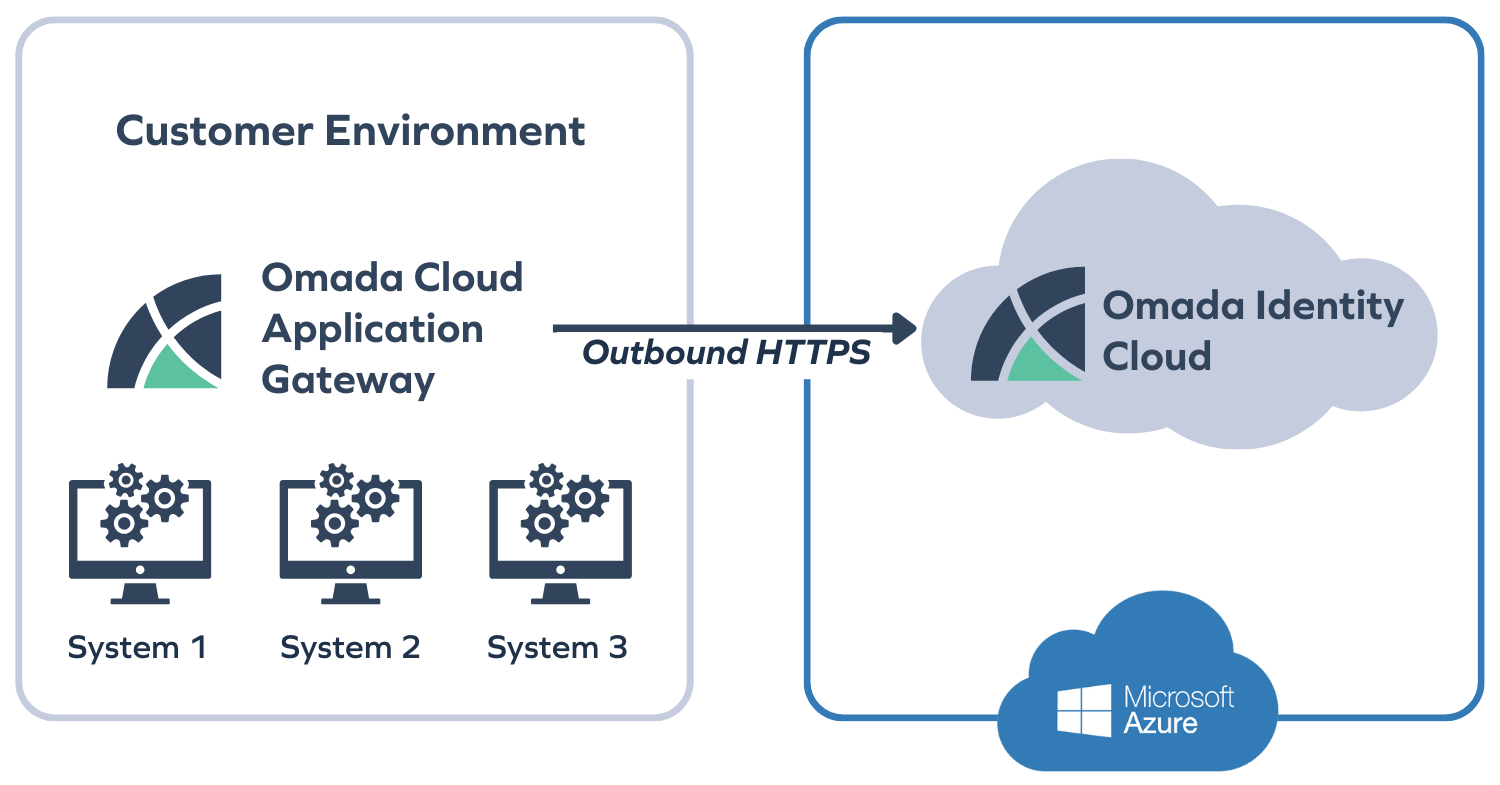
Secure, software‑defined connectivity for Omada Identity Cloud
The Cloud Application Gateway (CAG) delivers cloud-native connectivity aligned to Zero Trust with customer-controlled encryption keys and lightning-fast deployment.
The Cloud Application Gateway is a lightweight, software-defined service purpose-built to extend identity governance across distributed environments. It establishes secure outbound HTTPS sessions only when needed, avoiding complex firewall changes or persistent tunnels. It updates automatically to reduce maintenance and ensure future compatibility. Compared to competing solutions, it delivers faster time-to-value, lower operating overhead, and stronger security with customer-controlled encryption keys.

Deploy CAG alongside the systems you need to govern. Run on your preferred OS, hypervisor, or in containers. It is flexible and extensible across environments. Rollout is simple and automatic updates keep operational overhead low.

Avoid broad network exposure. CAG provides application and identity level access only when needed, minimizing attack surfaces and ensuring consistent policy enforcement across hybrid application and infrastructure

Use your own private encryption keys stored in your vault. Secrets remain encrypted with keys only you manage, reinforcing a zero knowledge posture and ensuring full compliance with your governance and security standards
Both models provide secure connectivity for Omada Identity Cloud connectors, but each serves different needs.
CAG is the right fit when agility and simplicity matter most. It enables rapid onboarding without complex firewall reconfiguration using secure outbound-only sessions that work anywhere. Ideal for organizations adopting Zero Trust, it limits access to what’s needed, reduces risk, and scales easily across hybrid environments. For teams that want control of encryption keys and low operational overhead, CAG is the natural choice.
VPNs are best suited for organizations with an established network infrastructure and strict regulatory requirements that mandates perimeter-based security enforcement. They provide benefits such as centralized control, IPsec logging, and strict routing isolation. If your environment depends on rigid segmentation and your team can manage tunnels and firewall changes, VPNs remain a dependable option.
| Feature | Cloud Application Gateway | VPN |
|---|---|---|
| Setup complexity | Low | Moderate to high |
| Zero Trust alignment | High | Low |
| Encryption | End-to-end encryption | Encrypted in the VPN stack |
| Network changes required | No | Yes |
| Scaling across sites | Fast | Network dependent |
| Perimeter control | Identity level trust | Network perimeter |
| Ideal use cases | Agile, hybrid environments | Established perimeter, regulated environments |
FEATURED RESOURCES
This guide aims to inform organizations how to successfully deploy and maintain an identity governance solution and realize the security, compliance, and efficiency benefits needed to run their business.
Extending identity governance across hybrid environments requires a deliberate integration strategy. Cloud Application Gateways offer agility and Zero Trust alignment.
Reliable modern IGA solutions can enable secure, compliant, and efficient access to data, applications and infrastructure. Learn more about Omada Identity Cloud.



